The SCR Malware Hack Explained
An in-depth examination of the malware and how to protect yourself
Malicious malware has been circulating on Twitter, Email, Instagram, and Discord in recent days, stealing people's Metamask money, tokens, and credentials. You may have already heard about or someone suspicious reached out to you.
In this article, we'll take a closer look at this malware and how it operates but also what you can do to protect yourself against it.
An introduction to social engineering
Hackers are using social engineering tricks to get their victims to click a link, download files and install a piece of software but what is social engineering exactly?
Let’s start exploring.
Social engineering is the art of manipulating someone to provide sensitive information through human interactions.
To carry out an attack, an attacker first examines the targeted victim to obtain relevant background information such as personal information, potential points of entry, and cryptocurrency balance information from a public wallet for example. They're hunting for any sort of information they can get their hands on in order to use it against you.
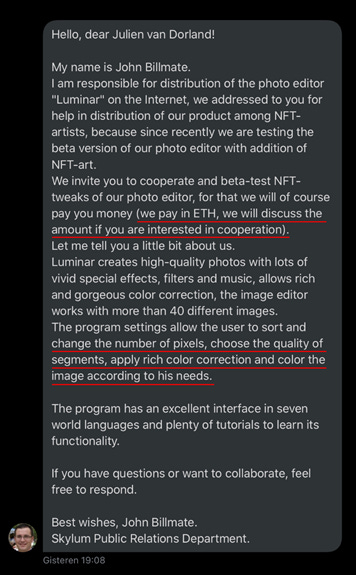
This attacker sent me a DM on Twitter. You can see that this message instantly raised a handful of red flags. Let's take a closer look at it.
According to the attacker, payment would be made in ETH. Let’s use common sense here. The majority of businesses do not pay in ETH and instead use a fiat currency. This was the first red flag I saw. The attacker also described adjusting the number of pixels, using rich color correction, and coloring the image to your liking. Let's go back to where I discussed what social engineering is for a second. The attacker did their research to learn more about the type of artwork I create, which is abstract multi-colored work with sorted pixels, exactly what the attacker is mentioning.
Another screenshot from the conversation. As you can see, the attacker cited one of my artworks, ‘'Vision" indicating that they are well-versed in my work. They referred to me as a professional, which is why they came to me. Again, the goal is to establish trust with their victim. The attacker provided me a link to a website. When I looked at this website, I discovered that it was a direct clone of the real version of the application described.
Artists who are well-known in the community are also being targeted. This was accomplished using the same manner as previously explained. As you can see, an attacker attempted to contact the artist as a client or to collaborate on a project. Finally, the attacker sent a password-protected ZIP or RAR file containing some information about their fake project. It also included an SCR file, but what is it exactly and how has it impacted so many artists? Let's dig a little deeper.
What is an SCR file?
An SCR file is a screensaver that Windows uses to save energy. It contains a graphic, animation, slide show, or video that you can use as a Windows screensaver. These Windows screensavers were initially designed to extend the life of CRT and plasma display monitors. If a user has specified a screensaver in Windows' display properties, the system will automatically activate the user's selected screensaver when the Windows machine has been inactive for a specific amount of time. This is done to keep the power consumption of these display devices to a minimum.
SCR files are executable files, you should not open or use them as a screensaver unless you can verify their legitimacy and source. Viruses and other malware have been reported to be found in SCR files received from sources other than Windows. They're tucked away / packed executable files containing a virus.
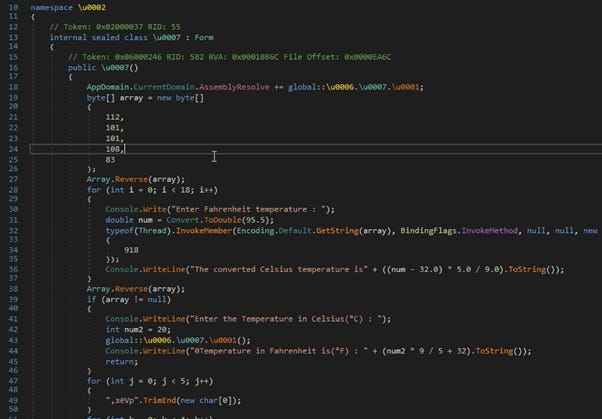
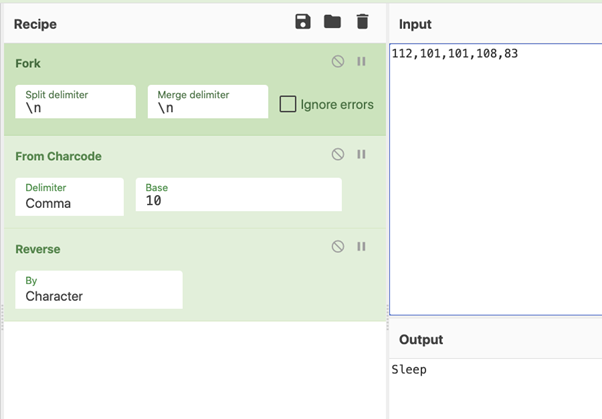
The SCR malware analysis
We had an extensive look at a couple SCR files are going around. Thanks to Colin Hardy for helping me reverse engineering this malware. More malware analysis and related videos may be found on his YouTube channel here.
The SCR samples
Paper Collective collaboration offer.pdf
MD5 = 657ae210e43b21270594476e124411fa
Collaboration terms.rar
Password: 2021
MD5 = bdef810a7db49ca29dc148a41bd0b566Collaboration terms .scr
MD5 = 8e74d3bf5e3fc0b959bfcd4964a6d842



Shi-woo Bok.zip
Password: Shi-woo
MD5 = 780c118f632a1387fccf206ebba8b668
Included files within the ZIP
I'm wearing a mask (you could try the cyberpunk theme).jpg
MD5 = a6296e3bf7377a7f7928045056afdbbc
Me and my open face.jpg
MD5 = e31d994a70b4e0b3ab6adabde919466e
You can use these colors as a basic idea.jpg
MD5 = 59349c12b8ae80656051078ffd9501eb
animated background.scr
MD5 = fd86251ef48842e8d6f60cbef01eebce
Which credentials does it steal?
The malware that has been circulating in the NFT community offers a wide range of capabilities. It is capable of stealing virtually everything you have saved on your computer. Here's a list of what it steals from you.
Sensitive system information:
IP
Country
City
Current PC username + HWID
Keyboard layouts
Screenshots of the screen
Screen resolution
Operating system
UAC settings
Malware admin access
User-Agent information about the components of the PC (video cards, processors)
Installed antiviruses
Cryptocurrency wallet information:
YoroiWallet
Tronlink
NiftyWallet
Metamask
MathWallet
Coinbase
BinanceChain
BraveWallet
GuardaWallet
EqualWallet
JaxxxLiberty
BitAppWallet
iWallet
Wombat
AtomicWallet
MewCx
GuildWallet
Software information:
Steam credentials
Telegram credentials
FTP (FileZilla) credentials
Discord token
All browser passwords/creditcards/cookies on Chromium (Chrome etc.)
All browser passwords/creditcards/cookies running on Gecko (Mozilla etc.)
How to protect yourself
Step 1 - Manage your passwords properly
Back up your passwords with a program like 1Password or Dashlane, and never use the same password twice! Credentials obtained from hacked databases are subsequently being sold on hacker forums. This gives hackers the ability to crack your accounts if you use the same password.
Tip: You can check if your passwords and personal data got leaked in one of the of major breached databases here.
Step 2 - Use Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a technique of gaining access to an online account or computer system that requires the user to provide two distinct pieces of information.
Do not use SMS 2FA but use Authy or Google authenticator
Use 2FA on all of your accounts, especially your email
Tip: Change your email password first if your accounts are compromised and you do not have 2FA enabled. Your email is the most valuable account since it is linked to all of your other online accounts.
Step 3 - Use a hardware wallet
Hardware wallets provide you ownership and control over your digital holdings. However, with tremendous power comes tremendous responsibility: running your own bank is not easy and needs discipline. The use of a hardware wallet does not make you immune to social engineering, physical dangers, or human mistakes. Use common sense and fundamental security standards at all times.
I recommend Trezor or Ledger as your hardware wallet. It’s important that you purchase these from official websites such as ledger.com and trezor.io for better security. Examples of different phishing scams can be found here.
Tip: If you don't want to display your transaction history and address to the public, you may want to send your tokens to an exchange first, such as Binance or Coinbase, and then move them to your hardware wallet.
Step 4 - Keep your seed phrase safe and secure
After setting up your hardware wallet, you will have to secure the seed phrase that came with it. But how do you do that? Your seed phrase is your responsibility for the safety and availability of your whole wallet.
Do not take a picture of your seed phrase
Do not store it anywhere digitally on your computer or phone
Never share your seed phrase with anyone
Tip 1: Paper and ink degrade over time, utilize a backup tool like Trezor's Cryptosteel, which is a capsule of solid steel for extra security. You can also engrave your seed phrase on a steel plate or laminate it.
Tip 2: Make two copies of your seed phrase and keep one in a separate location. Water or fire damage to your seed phrase card and house could occur as a result of natural disasters.
Step 5 - Enable file extensions
It is a good idea to configure Windows to display file extensions for security reasons. For example, the .exe file extension is one of many that Windows uses as a program. If you can't see the extension of a file, it's difficult to know whether it's a program, a safe document, or a media file. Hackers can modify the icon of a program so please enable this setting.
Here is how to enable file extensions:
Step 6 - Do not trust email domains blindly
Email domain names can be faked by an attacker and reach your inbox when sent correctly. These emails will not appear in the spam folder. You need to learn to read email headers to ensure that the email comes from a trusted domain. Click here to learn more about how to read email headers.
Step 7 - Install antivirus software
Antivirus software is a data security tool that is installed in a computer system to defend it against viruses, spyware, malware, rootkits, trojans, phishing attacks, spam assaults, and other online cyber threats.
I recommend installing Malwarebytes and scan your PC regularly. They offer a premium trial version that works very well. It is not necessary to purchase a premium version of it after the trial period ended because once the trial time has expired because the free version of this antivirus is as effective.
Tip: Check your downloaded files before opening and installing them for any virusses by scanning them online using VirusTotal.
Step 8 - Be aware of known scams
Scams are taking place everywhere but most of the time on Discord, Twitter, Instagram, and by email. Never send money to someone you don't know and always verify the source. Don’t trust, verify.
I’m hacked! What happens now?
If you opened and executed the SRC or EXE file on your computer and your credentials were compromised, here's what you should do.
Stay calm and don't panic. Your credentials may have been stolen, but if you have two-factor authentication set, the attacker won't be able to do much with them. Because your email password is linked to all of your other accounts, you should always update this password first.
Look for any suspicious EXE files that are currently running in task manager. Make sure to end those activities as soon as possible and remove these files you've downloaded from your computer.
You can back up your files and reinstall windows. Remove your computer from the internet and start your Windows machine in safe-mode to create a backup of your files.
Thank you for reading!
Consider following me on Twitter for valuable updates and information about NFTs. I’m a Digital Artist and NFT collector. You can find all of my links here: https://julien.pro/links











well done!! very clear
Similar SCAM happening now from this email advertising@mvmt-mkt.com from a 'Sofia Nelson' targeting design and marketing agencies across Australia.